RBAC, ABAC, and Beyond: Different Models of Access Control Explained

In today’s digital world, every system, from small web apps to enterprise platforms, faces a critical question:
Who should be allowed to do what?
Whether it’s a finance dashboard, a cloud resource, or a shared document, access control is what ensures that the right people have the right access at the right time.
It’s the backbone of cybersecurity, compliance, and operational integrity.
But as organizations grow and systems become more complex, simple permission checks no longer cut it.
That’s where structured access control models like RBAC, ABAC, and PBAC come in.
In this guide, we’ll explore:
- The main access control models (and how they differ)
- When to use each one
- The pros and cons of each approach
- How modern systems blend multiple models for flexibility and security
Let’s break them down from the simplest role-based approach to the most adaptive policy-driven systems.
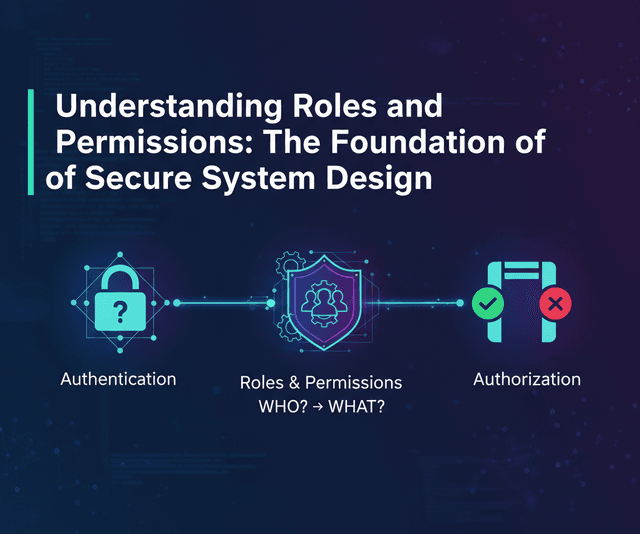
What Is Access Control?
At its core, access control is about managing who can access what resources under which conditions.
It’s the practical side of authorization enforcing rules after a user has been authenticated.
| Step | Concept | Example |
|---|---|---|
| Authentication | Confirms who you are | Logging in with username and password |
| Authorization | Decides what you can do | Checking if you’re allowed to access a settings page |
Without effective access control, even authenticated users might view or modify data they shouldn’t leading to leaks, compliance violations, or system compromise.
1. Role-Based Access Control (RBAC)
RBAC (Role-Based Access Control) is one of the most widely used and practical access control models in modern systems. It assigns permissions based on roles, which represent a group of users who share similar responsibilities, duties, or levels of authority.
Instead of granting permissions to each user individually which quickly becomes unmanageable RBAC introduces an abstraction layer: roles.
A role acts as a bridge between users and permissions, ensuring consistency, scalability, and ease of management.
| Concept | Example |
|---|---|
| User | Amina |
| Role | Manager |
| Permissions | view_reports, edit_team, approve_budget |
In this setup, Amina doesn’t directly have those three permissions , she inherits them through her Manager role.
If another user, like Ali, is also assigned the Manager role, he immediately gains the same capabilities. That means administrators can manage access at the role level rather than micromanaging every user.
How RBAC Works
RBAC operates on a simple but powerful mapping:
User → Role → Permissions
This three-step relationship allows system administrators to:
- Define roles that mirror real-world job functions (e.g., Salesperson, Engineer, Admin).
- Assign permissions (e.g.,
create_invoice,view_customer_data,delete_user) to each role. - Assign users to those roles.
When a user logs in and tries to perform an action, the system checks:
- Which roles the user has
- Which permissions those roles provide
If the required permission is included in any of the user’s roles → access granted ✅
If not → access denied 🚫
This model simplifies authorization logic and makes it auditable, predictable, and compliant.
Why RBAC Matters
RBAC brings order and structure to access management, especially as systems grow.
Imagine a company with hundreds of employees and dozens of applications, giving and revoking permissions manually for each person would be a nightmare.
RBAC solves this by grouping permissions logically:
- When a new employee joins, assign them a predefined role.
- When someone changes departments, switch their role.
- When someone leaves, revoke their role instantly removing access everywhere.
This ensures access is consistent, traceable, and easy to review; key principles of good security and compliance.
Types of Roles in RBAC
In real-world systems, not all roles are equal. RBAC often includes several layers of role types:
-
Functional Roles – Represent job functions (e.g., Sales Rep, Accountant, HR Assistant).
- Define what users do day-to-day.
- Example:
HR Assistantcanview_employee_recordsandupdate_leave_status.
-
Administrative Roles – Represent elevated privileges (e.g., Admin, Security Officer).
- Manage configurations, users, and high-impact settings.
- Example:
System Admincancreate_user,assign_role,delete_user.
-
Hierarchical Roles – Some roles inherit permissions from others (role hierarchy).
- Example:
Each role includes the permissions of the one below it.Employee → Manager → Director → Administrator
- Example:
-
Contextual Roles – Activated only in certain scenarios or timeframes.
- Example:
Shift Supervisoractive only during scheduled hours.
- Example:
These role structures make RBAC adaptable to both small teams and large enterprises.
Advantages
✅ Easy to manage: Roles act as reusable templates for permissions. Instead of configuring dozens of users individually, administrators can manage access in bulk by updating a single role.
✅ Organized and consistent: RBAC reflects the real-world structure of an organization. Each department or job title maps naturally to a role, making the system intuitive and self-documenting.
✅ Scalable : RBAC scales beautifully. Whether you have 10 users or 10,000, the role system remains manageable, new hires simply inherit permissions by joining the right role.
✅ Compliant and auditable: Most regulatory frameworks (ISO 27001, SOC 2, HIPAA, PCI-DSS) require clear access management and audit trails. RBAC makes this possible by keeping a record of who holds which role and what each role can do.
✅ Least Privilege Support: RBAC naturally supports the Principle of Least Privilege giving users only the access they need for their role, and nothing more.
Drawbacks
⚠️ Limited flexibility: RBAC decisions are static. They don’t consider context like time of day, device type, location, or data sensitivity. For example, RBAC alone can’t express “Managers can approve expenses only during business hours” — that’s where ABAC comes in.
⚠️ Role explosion: In large or dynamic environments, you might end up creating dozens of near-identical roles (e.g., Manager_North, Manager_South, Manager_Online), which can become difficult to manage and audit.
⚠️ Not context-aware: RBAC doesn’t easily adapt to changing environments or temporary conditions (like contractors, temporary projects, or sensitive data classifications).
Real-World Example
Let’s take a project management system:
| Role | Permissions |
|---|---|
| Team Member | view_tasks, update_own_tasks |
| Project Manager | view_tasks, update_tasks, assign_tasks, approve_deliverables |
| Admin | All permissions, including create_user, delete_project, manage_roles |
Here’s how it plays out:
- A Team Member can update only their own assigned tasks.
- A Project Manager can manage all team tasks and approve deliverables.
- An Admin oversees the entire system and manages user accounts.
So when Amina, a Project Manager, logs in and tries to approve a deliverable:
- The system checks Amina’s role → Manager
- It verifies that
approve_deliverablesis included in that role’s permissions - If yes → the action succeeds
- If not → access is denied
RBAC provides a clear, scalable, and auditable way to manage authorization. It’s simple enough for small systems yet robust enough for enterprise-scale governance, which is why it remains the most common access control model in the industry.
2. Attribute-Based Access Control (ABAC)
ABAC (Attribute-Based Access Control) is a dynamic, context-aware model that grants or denies access based on a combination of attributes — properties that describe the user, the resource, the action, and the environment.
Unlike RBAC, which focuses on static job roles, ABAC evaluates access in real time using multiple factors.
It doesn’t just ask “Who are you?” but also “What are you trying to access?”, “Where are you?”, and “Under what conditions?”
| Attribute Type | Description | Example |
|---|---|---|
| User Attribute | Characteristics of the person or system requesting access | department = HR, job_title = Analyst, clearance = Confidential |
| Resource Attribute | Information about the object or data being accessed | type = document, classification = confidential, owner_department = HR |
| Action Attribute | The operation being attempted | action = view, action = edit, action = delete |
| Environment Attribute | Contextual details about the access event | time = 10:00 AM, location = office, device = corporate_laptop |
A sample ABAC policy might look like this:
“Allow access if user.department = resource.department and time is within 9 AM–5 PM and device is corporate-managed.”
This enables organizations to make authorization decisions that adapt automatically to context and changing conditions.
How ABAC Works
ABAC uses logical policies (if-then statements) that evaluate attributes in real time. When a user attempts to perform an action, the system gathers the relevant attributes from identity systems, resources, and the environment, then checks them against predefined policies.
A simple policy might look like this:
IF user.department = resource.department
AND user.clearance >= resource.classification
AND environment.time BETWEEN 09:00 AND 17:00
THEN permit access
If all conditions are met → Access Granted ✅
If not → Access Denied 🚫
This means access isn’t determined by fixed roles, but by a dynamic combination of factors that reflect who the user is, what they want to do, and the current context.
Why ABAC Matters
As organizations move toward cloud, hybrid, and distributed systems, static roles can no longer handle the complexity of real-world access needs.
Employees, contractors, and partners may belong to multiple teams, work remotely, or switch contexts frequently.
ABAC provides fine-grained, adaptive control that responds to real-world variables automatically.
For example:
- A financial analyst can view sensitive reports only during business hours and only from a company laptop.
- A contractor’s access automatically expires when their
contract_end_dateattribute changes. - A doctor can view a patient’s record only if they are the assigned physician and the patient is currently admitted.
This makes ABAC ideal for large enterprises, cloud-native systems, and regulated industries where security must adapt in real time.
Real-World Example
Let’s imagine a Human Resources management system.
A typical ABAC policy could be:
“Allow access to employee records only if:
- The user’s department matches the record’s department
- The user’s clearance level is equal to or higher than the record’s classification
- The request is made during office hours (9 AM–5 PM)
- The device used is company-managed”
So:
- ✅ An HR employee in the HR department viewing records from their corporate laptop at 10 AM is granted access.
- 🚫 That same employee accessing the same data from a personal tablet at 8 PM is denied.
- 🚫 An IT administrator, despite having high system privileges, can’t access HR data unless their attributes meet the HR policy conditions.
This contextual logic makes ABAC far more flexible and secure than static, role-based systems.
Advantages
✅ Dynamic and Context-Aware: ABAC adapts to changes automatically, access can depend on location, time, device, or even system risk score. No manual role updates are needed.
✅ Fine-Grained Control : Policies can define very specific conditions, down to individual data fields or records, enabling powerful and precise access rules.
✅ Eliminates Role Explosion: Instead of creating dozens of overlapping roles (like Manager_Mogadishu, Manager_Nairobi, etc.), ABAC uses attributes (like user.region = resource.region) to control access dynamically.
✅ Centralized and Consistent: Policies can be managed in one place and enforced across multiple systems, ensuring consistency across your entire organization.
✅ Ideal for Compliance: Auditors can review clearly defined policies instead of sprawling role lists, making ABAC suitable for frameworks like GDPR, HIPAA, and ISO 27001.
Drawbacks
⚠️ Complex to Implement: ABAC requires a robust identity system and consistent attribute management. Missing or outdated attribute data can break policy enforcement.
⚠️ Harder to Audit and Explain: Because access is calculated dynamically, it can be difficult to quickly determine why a specific decision was made without reviewing logs and attributes.
⚠️ Policy Conflicts: With many overlapping conditions, poorly written or conflicting policies can cause unpredictable access behavior.
⚠️ Performance Overhead: Each decision requires multiple lookups and condition evaluations, which can add latency in high-traffic environments.
Example Scenario
Consider a company’s document management platform:
| Attribute | Example |
|---|---|
| User.department | Marketing |
| User.clearance | Medium |
| Resource.department | Marketing |
| Resource.classification | Low |
| Environment.location | Office |
Policy:
“Allow access if user.department = resource.department
and user.clearance ≥ resource.classification
and location = Office.”
Results:
- ✅ Marketing employee in the office → Access Granted
- 🚫 Marketing employee at home → Denied (environment fails)
- 🚫 HR employee → Denied (department mismatch)
This demonstrates ABAC’s flexibility access decisions are made in real time based on context and data.
In essence:
- RBAC defines who generally can do what based on roles.
- ABAC defines who can do what, when, where, and under what conditions based on real-time attributes.
ABAC provides unmatched flexibility and precision, but requires discipline in policy design and attribute management.
For many organizations, the ideal solution is a hybrid model: using RBAC for structure and ABAC for adaptive, context-aware control.
3. Policy-Based Access Control (PBAC)
PBAC (Policy-Based Access Control) is an advanced and highly flexible model that manages authorization decisions using centralized policies; logical rules that define who can perform what actions under which conditions.
Unlike RBAC (role-based) or ABAC (attribute-based), which both rely on internal data structures like roles or attributes, PBAC externalizes the decision-making process into explicit policies.
These policies are stored, versioned, and enforced consistently across multiple systems through a policy engine.
A simple PBAC policy might be:
“Deny access to archived projects for all users.”
Policies can reference roles, attributes, context, or system states, and are typically written in structured formats or languages such as:
- XACML (eXtensible Access Control Markup Language): XML-based policy standard.
- Rego (Open Policy Agent): Modern, lightweight policy language widely used for cloud and Kubernetes environments.
- Cedar (AWS IAM): A policy language developed for AWS fine-grained permissions.
These systems separate policy definition from policy enforcement, creating a unified way to manage access decisions across applications and platforms.
How PBAC Works
At the heart of PBAC is the Policy Decision Point (PDP) a central engine that evaluates policies against incoming requests.
When a user or system requests an action, PBAC performs these steps:
- Policy Information Point (PIP): Collects relevant data like user attributes, resource metadata, environment conditions.
- Policy Decision Point (PDP): Evaluates the policy logic using this data.
- Policy Enforcement Point (PEP): Enforces the decision either allowing or denying access.
This flow is often summarized as:
Request → PEP → PDP → Decision → PEP → Allow/Deny “Allow a user to delete a project if the project is active and they are assigned as the owner.”
Here, the system retrieves:
- The project’s status (active or archived)
- The requesting user’s identity and relationship to the project
Then the PDP applies the policy logic to decide.
PBAC allows policies to be dynamic, version-controlled, and language-agnostic, meaning multiple systems can share the same central decision framework.
Why PBAC Matters
In large, distributed environments, managing access rules across many systems can become fragmented and inconsistent. PBAC solves this by centralizing authorization logic — providing a single source of truth for access policies.
This approach is essential for:
- Enterprises managing hundreds of services or microservices
- Cloud-native platforms that need consistent enforcement across APIs, Kubernetes, and CI/CD pipelines
- Compliance-heavy industries that require auditable, explicit, and testable access rules
PBAC ensures every access decision is made based on consistent logic, no matter where or how it’s enforced.
Real-World Example
Let’s say your company manages digital projects in a multi-tenant SaaS platform.
A PBAC policy could look like this:
“Allow users to edit a project only if:
- The project is not archived
- The user is the project’s owner
- The user’s account is active
- The environment is production, not staging”
Expressed as logic:
IF resource.status != "archived"
AND user.user_id = resource.owner_id
AND user.status = "active"
AND environment.env_name = "production"
THEN permit edit_project
The policy engine evaluates these conditions every time an edit request is made, ensuring rules remain consistent across all APIs, dashboards, and services.
Advantages
✅ Highly Flexible and Expressive: PBAC can express any combination of conditions from role-based permissions to context-aware logic using formal rules and languages.
✅ Centralized Management: Policies are stored in a central repository and applied across multiple systems. This ensures consistent access decisions, even in complex, distributed environments.
✅ Auditable and Transparent: Policies are written as declarative logic, making them human-readable, version-controlled, and reviewable, ideal for compliance and governance.
✅ Separation of Concerns: Developers build applications; security teams manage policies independently. Access rules can be changed without redeploying code.
✅ Scalable and Testable: PBAC integrates with CI/CD pipelines — policies can be tested and validated just like software, improving reliability at scale.
Drawbacks
⚠️ Higher Complexity: PBAC introduces a dedicated policy framework (e.g., OPA, XACML), requiring additional setup, tooling, and expertise.
⚠️ Governance Overhead: Managing hundreds of distributed policies requires strong naming conventions, ownership models, and review processes.
⚠️ Potential Performance Cost: Centralized policy evaluation can add slight latency if not properly cached or distributed.
⚠️ Overkill for Smaller Systems: For small apps or teams, PBAC’s sophistication may outweigh its benefits a simpler RBAC or hybrid model might suffice.
Example Scenario
Consider an enterprise that manages multiple systems (CRM, analytics, HR, finance). Each has different access needs, but security policies must remain consistent organization-wide.
Instead of implementing separate access logic in each system, PBAC allows all to query a centralized policy engine, for example:
“Allow read access to financial reports only if:
- The user’s department = Finance
- The report’s sensitivity = Low or Medium
- The request originates from an internal network”
This rule is written once and reused across all applications; no duplication, no inconsistencies.
Result:
- ✅ A Finance manager accessing from the office → Access Granted
- 🚫 A Marketing user → Access Denied
- 🚫 A Finance user on a personal laptop outside the network → Access Denied
PBAC ensures consistent decisions everywhere with minimal code changes in each app.
In short:
- RBAC focuses on roles.
- ABAC focuses on attributes.
- PBAC focuses on policies: logical rules that can include both roles and attributes.
PBAC offers the most flexibility and control of all three models, making it ideal for modern, cloud-native, and compliance-driven organizations. It turns access management from static configuration into programmable, testable logic making authorization as agile as the systems it protects.
4. Other (and Emerging) Models
While RBAC, ABAC, and PBAC are the most common, others play key roles in specialized contexts.
| Model | Description | Typical Use Case |
|---|---|---|
| MAC (Mandatory Access Control) | Central authority enforces strict access levels | Military and classified systems |
| DAC (Discretionary Access Control) | Resource owners control who can access their assets | File-sharing and collaboration tools |
| ReBAC (Relationship-Based Access Control) | Access depends on relationships between entities | Social media, project collaboration platforms |
Comparing the Models
| Model | Control Basis | Flexibility | Common Use Case | Example Rule |
|---|---|---|---|---|
| RBAC | Roles | Medium | Internal systems, SaaS dashboards | “Admins can manage users” |
| ABAC | Attributes | High | Enterprise and cloud apps | “Allow if user.department = resource.department” |
| PBAC | Policies | Very High | Regulated and large-scale systems | “Deny access if resource.status = archived” |
| MAC | Security classification | Low | Government/military systems | “Top secret files only for clearance level ≥ 5” |
| ReBAC | Relationships | Contextual | Social or collaborative systems | “Allow if user is a collaborator” |
Choosing the Right Model
✅ For Simplicity: RBAC
Ideal for startups or small apps that need a clear, role-based structure.
🧠 For Contextual Control: ABAC
Great for organizations that need to consider department, location, or data type.
🏢 For Central Governance: PBAC
Perfect for large enterprises with multiple systems and compliance needs.
| Organization Size | Recommended Model |
|---|---|
| Small startup | RBAC |
| Mid-size company | ABAC |
| Large enterprise | PBAC or hybrid (RBAC + ABAC) |
Summary: Key Takeaways
| Concept | Description |
|---|---|
| RBAC | Role-driven, simple, and easy to manage |
| ABAC | Attribute-driven, flexible, and context-aware |
| PBAC | Policy-driven, centralized, and auditable |
| MAC/DAC/ReBAC | Specialized for strict or relationship-based control |
Access control models define how trust is managed in digital systems. Choosing the right one depends on your system’s complexity, scale, and risk tolerance. Start simple, grow strategically, and ensure your access policies evolve as your organization does.
Modern security isn’t just about keeping people out — it’s about letting the right people in, the right way.
References
-
NIST Special Publication 800-162 — Guide to Attribute Based Access Control (ABAC) Definition and Considerations
-
NIST Special Publication 800-192 — Verification and Test Methods for Access Control Policies/Models
National Institute of Standards and Technology (NIST), 2017. -
Hu, V. C., Ferraiolo, D., Kuhn, D. R., et al. — Attribute-Based Access Control (ABAC): An Overview and Current Status
-
OASIS XACML Technical Committee — eXtensible Access Control Markup Language (XACML) Version 3.0
-
Open Policy Agent (OPA) — Policy-based control for cloud-native environments CNCF Project Documentation.
-
AWS Cedar Policy Language — Fine-grained authorization for AWS and custom applications
Amazon Web Services, 2023. -
Microsoft Azure Documentation — Overview of Role-Based and Attribute-Based Access Control in Cloud Environments.